Introduction to Security Testing
In the current digital environment, characterized by the proliferation and escalating sophistication of cyber threats, safeguarding systems and data has never been more vital. This all-encompassing manual will examine the realm of security testing, highlighting its significance in the era of cyber threats and imparting insightful information on prevalent vulnerabilities, optimal methodologies, tools and techniques, regulatory factors, and additional pertinent topics.
Understanding the Importance of Security Testing in the Age of Cybersecurity Threats
Increasing cases of cyber-attacks and data leaks make it clear to enterprises that safety assessment matters. But just using traditional security tools like firewalls and anti-virus software is no longer enough. Meanwhile, measures to prevent such weaknesses from being exploited by evil forces must be adopted.
Security testing is also an indispensable step in maintaining customer trust, protecting client privacy, and ensuring business continuity. By testing their systems, applications, and networks tirelessly in this way organizations can discover chinks in their armor that a cybercriminal might try to exploit. Taking such action allows the organization to put in place suitable security procedures and minimize possible dangers, ultimately strengthening its overall defense.
Also Read: The Evolving Landscape Of Software Testing Services: Current Trends And What Lies Ahead
Different Types of Security Testing
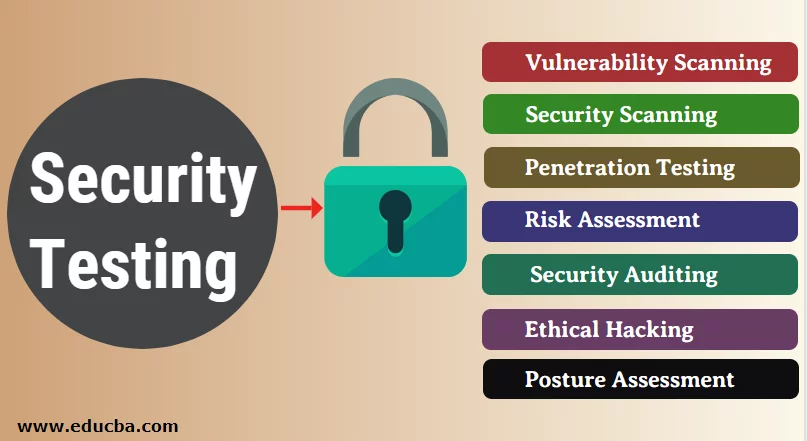
Security testing comprises a multitude of methodologies and techniques that are designed to assess the resilience of the security measures implemented by an organization. The following are examples of prevalent forms of security testing:
Vulnerability Scanning: This form of testing scans systems and networks for known vulnerabilities through the utilization of automated tools. It facilitates the detection of vulnerabilities that may be targeted by malicious actors.
Penetration Testing: Penetration testing, which is also referred to as ethical hacking, involves the simulation of authentic assaults to discover weaknesses in networks, systems, or applications. It encompasses a methodical and regulated strategy to capitalize on vulnerabilities and offer suggestions for improvement.
Security Code Review: This procedure identifies potential security defects, such as insecure coding practices or exploitable vulnerabilities, through a comprehensive examination of the source code.
Security Architecture Review: This form of assessment evaluates the policies, procedures, and controls that comprise the organization’s overall security architecture. It facilitates the identification of vulnerabilities and offers suggestions for improving the overall security stance.
Security Awareness Training: Security awareness training, although not conventional testing, is critical for ensuring that personnel comprehend the significance of security and possess the necessary skills to effectively address prospective threats.
Common Security Vulnerabilities and How to Detect Them
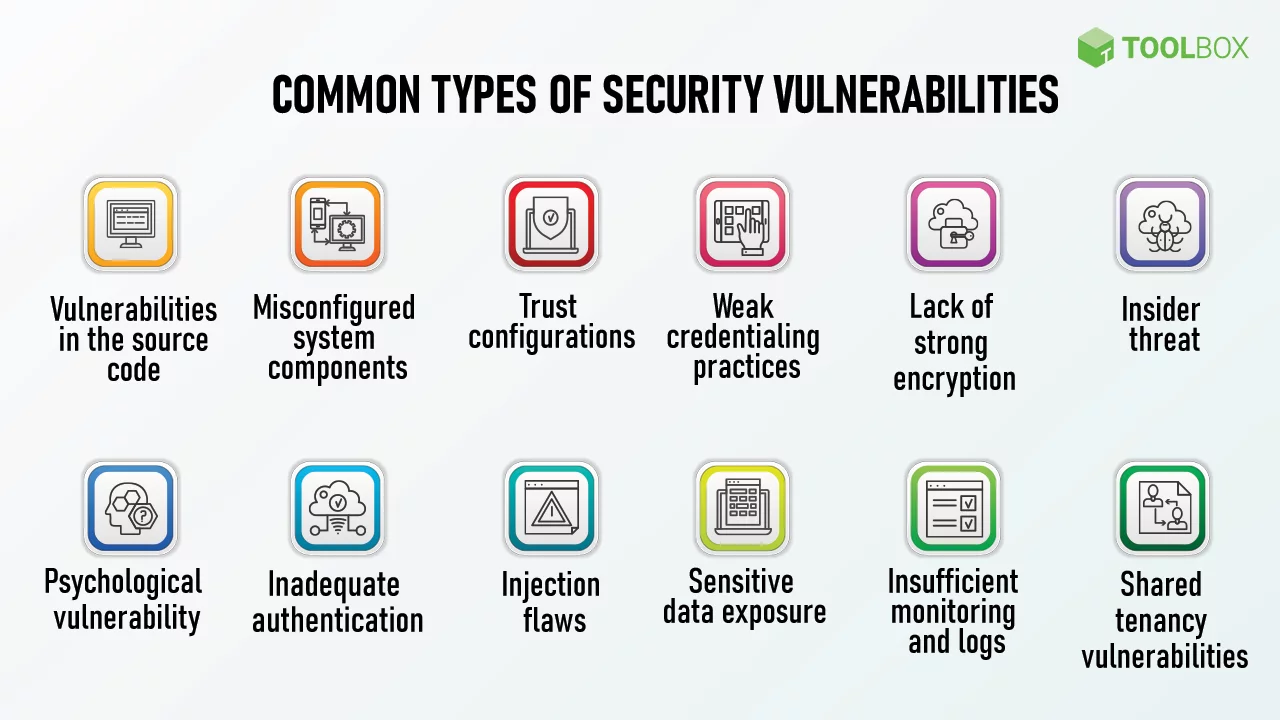
Notwithstanding the progress made in cybersecurity measures, prevalent vulnerabilities persist in presenting substantial hazards to organizations. Understanding these vulnerabilities and the methods to identify them is critical for conducting effective security testing. The following are some of the most prevalent security vulnerabilities:
Injection Attacks: Injection attacks transpire when an interpreter receives untrusted data incorporated within a command or query, thereby precipitating inadvertent execution. Input validation and parameterized queries are two methods that can be utilized to detect and avert injection attacks.
Cross-Site Scripting (XSS): Vulnerabilities in XSS enable malicious actors to inject harmful scripts into user-facing web pages. By employing appropriate input validation and output encoding, XSS attacks can be identified and averted.
Cross-site request forgery (CSRF): CSRF assaults deceive users who have been authenticated into unknowingly performing malicious actions. Request validation and the implementation of anti-CSRF tokens can aid in detecting and preventing CSRF vulnerabilities
Insecure Direct Object References: Insecure direct object references are a security risk that manifests when an application discloses sensitive data or internal implementation details. User authorization mechanisms and appropriate access controls can aid in detecting and preventing insecure direct object references.
Security Misconfigurations: Security vulnerabilities may arise due to misconfigurations occurring in systems, applications, or network devices. Consistent configuration management and vulnerability analysis can aid in identifying and mitigating security misconfigurations.
Also Read: Ways to Secure Your Data When Working Remotely
Tools and Techniques for Security Testing
In the realm of security testing, numerous tools and techniques are available to assist organizations in identifying vulnerabilities and strengthening their defenses. Some popular tools and techniques include:
Within the domain of security testing, an extensive array of tools and methodologies exist to aid organizations in the detection of vulnerabilities and fortification of their defenses. Examples of well-known instruments and methods include:
Vulnerability Scanners: Nessus, OpenVAS, and Qualys are examples of automated tools that can scan networks and systems for known vulnerabilities.
Web application scanners, including Acunetix, Burp Suite, and OWASP ZAP, can assist in the detection of application-specific security defects, including SQL injection and XSS vulnerabilities.
Penetration testing frameworks, such as Cobalt Strike and Metasploit, offer extensive collections of resources and tools to facilitate the execution of penetration testing and the simulation of authentic attacks.
Static and dynamic code analysis can detect security defects, including vulnerabilities and insecure coding practices, using tools such as SonarQube and Veracode.
Threat Modeling: Typically performed during the design phase, this method identifies potential threats, vulnerabilities, and hazards to an application or system.
The Role of Security Testing in Compliance and Regulations

Organizations face a multitude of compliance obligations in the current regulatory environment, which are formulated to safeguard sensitive information and guarantee the confidentiality and safety of individuals. The execution of security testing is vital to fulfill these compliance responsibilities. Important regulatory factors to bear in mind encompass:
Payment Card Industry Data Security Standard (PCI DSS): PCI DSS mandates that organizations responsible for processing payment card data conduct routine vulnerability scanning and security testing.
According to the General Data Protection Regulation (GDPR), businesses have a responsibility to put in place suitable security measures for personal data. Security testing can help spot and address vulnerabilities that could lead to a data breach.
The Health Insurance Portability and Accountability Act (HIPAA) requires that healthcare organizations protect the privacy of their patients ‘medical information. Security testing secures patient information and compliance with HIPAA regulations.
ISO 27001 is a global standard that pertains to the administration of information security. Compliance with ISO 27001 requires security testing, which enables businesses to exhibit their dedication to preserving a secure environment.
Also Read: Why Are Encryption Important For Businesses?
Incorporating Security Testing into the Software Development Lifecycle
To ensure the effectiveness of security procedures, it is necessary to integrate testing for safety in all stages of software development (SDLC). Doing so allows organizations to uncover and fix vulnerabilities early in the development process, reducing significantly the chances of a security intrusion. The following are crucial stages in integrating security testing into the SDLC:
The necessary criteria Collecting: Determine the security prerequisites and integrate them into the comprehensive requirements documentation for the project.
Secure Design: Incorporate secure architectural designs and coding practices to reduce the likelihood of exploitable flaws.
Code Development: Code development involves the implementation of static code analysis and peer code evaluations as a means to detect and rectify security vulnerabilities.
Testing and Quality Assurance: Conduct exhaustive security testing to identify and remediate vulnerabilities, including vulnerability scanning, penetration testing, and security code evaluations.
Deployment and Maintenance: To ensure ongoing protection against emergent threats, implement continuous monitoring and routine security updates.
Benefits of Proactive Security Testing
Proactive security testing offers numerous benefits to organizations, including:
Risk Mitigation: By identifying weaknesses and fixing them before the bad guys can take advantage of those, organizations greatly reduce risk.
Cost Savings: Early detection and correction of vulnerabilities is cheaper than having to contend with the results of a security breach.
Enhanced Reputation: Through proactive testing, an organization exudes the image of its dedication to security. Customers and shareholders will have greater confidence in it as a result.
Compliance and Regulatory Adherence: Proactive security testing ensures compliance with industry regulations and helps organizations avoid potential penalties or legal repercussions.
Competitive Advantage: A robust security posture can differentiate an organization from its competitors and attract customers who prioritize data protection.
Security Testing Services and Providers
For organizations seeking external expertise or specialized services, numerous security testing providers offer comprehensive solutions tailored to specific needs. These providers offer a range of services, including:
Penetration Testing: Ethical hacking services that simulate real-world attacks to identify vulnerabilities and provide recommendations for remediation.
Vulnerability Assessments: Automated scanning services that identify known vulnerabilities in systems, applications, or networks.
Code Review: In-depth analysis of source code to identify security flaws and provide recommendations for improvement.
Security Consulting: Expert guidance and advisory services to help organizations develop and implement effective security strategies.
Also Read: 10 Ways 5G Shaping the Future for the Next Generation
Conclusion
In today’s era of constantly changing cybersecurity threats, organizations must take a proactive stance on security testing. Understanding the meaning of security testing, different kinds of testing, common vulnerabilities and ways to avoid risks; best practices for using tools and techniques-every step knowledgeable about this can help an organization build up its defenses against malicious intruders to protect systems in place. This is a process that they should actively pursue themselves.
As the driving force behind WikiPluck, I am dedicated to curating and sharing insightful knowledge across a spectrum of subjects. From technology trends to Business advice, WikiPluck strives to be a go-to resource for those seeking to enhance their understanding and make informed decisions.
Join me on this journey of discovery and enlightenment as we pluck the gems of wisdom from the vast landscape of knowledge.